Cryptojacking: You are making Money For Hackers!
Do you ever feel
the Internet is especially slow these days? Or have you ever wondered if maybe
it’s just your computer that’s getting slower?
Don’t rush to
the IT shop to buy a new computer yet … you may have been a victim of a new
trick used by malevolent hackers called browser “cryptojacking”
What is cryptojacking?
It’s a new trick
used to mine cryptocurrencies on your computer or mobile using your CPU
resources in the background without your knowledge when you
browse a compromised/infected website..
All that a cybercriminal has to do is load a
script into your web browser that contains a unique site key to force you to
enrich him.
Cryptocurrency
is mined, or produced, by solving complex mathematical puzzles. It’s like a
lottery: The more computing power you throw at the problems, the likelier you
are to win a reward. Every so often, a computer finds a solution and strikes
(digital) gold.
The script is
written in JavaScript (JS), so it is easy to embed into any web page.
Please note that
this technology was demonstrated in 2013 by a group of former MIT students who
created a company named TidBit
to distribute a BitCoin miner within a web browser
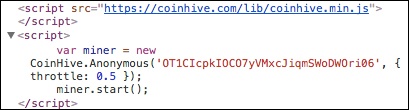
Here's an example of the code:
The above image is an
example of a code in which the publisher controls how much of its visitors' CPU
to utilize for mining (set by the throttle
number:0.5).
Cryptojacking scripts can
add to your processing load but it likely won't be enough for you to notice,
which is why cryptojacking remains under the radar. i.e throttle
number:0.5.
The script causes the browser/website to
"hijack" the user's CPU and use it to crack an encryption.
The website owner — and the script provider —
are paid, while the user typically does not benefit.
In fact, if the script uses enough of their
CPU, the quality of their browsing experience is likely to be reduced.
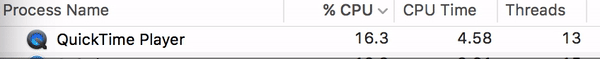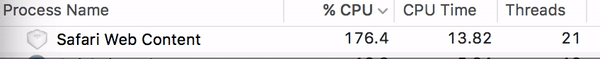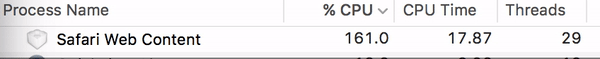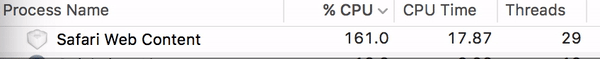
Watch
what can happen to your CPU when you visit one of the sites in question:
Microsoft spotted two new
services called CoinBlind and CoinNebula, both offering similar in-browser
mining services, with CoinNebula configured in such a way that users couldn't
report abuse.
Furthermore, none of these
two services even have a homepage, revealing their true intentions to be
deployed in questionable scenarios.
Examples of use of cryptojacking from the past couple of
weeks are when sites like PirateBay and Showtime had the CoinHive JavaScript
within their code.
The Pirate Bay, a
massively popular site that provides links to pirated movies, TV shows, and
music distributed via peer-to-peer torrent networks.
The Pirate Bay added a
crypto jacking code onto the site to tap into the huge computing power linked
through its users. Many people who actively use The Pirate Bay leave their
computers on nearly all day to download, upload, and share movies and TV shows
with others. With its built-in culture of sharing, one can only imagine how
much money the site was earning off the millions of people who
visit it every single day.
Also, a Web Store
extension known as SafeBrowse was also reported to use the same script.
Similar other sites that deployed
in-browser miners include Showtime, AirAsia, TuneProtect, and the official
website of soccer star Cristiano Ronaldo
On top of this, the cryptojacking craze has
also spread to WordPress plugins.
I spotted 3 plugins uploaded on the official WordPress
repo in the past week:
1.WP Monero Miner with Coin
Hive (now removed),
Mining Tools:-
hackers
developed the mining tools, such as Coinhive, JSEcoin, and Crypto-Loot.
The service took another step in the right
direction this week on Monday, when Coinhive launched AuthedMine, a service similar to the
original Coinhive service, but which won't start until the user clicks an
opt-in.
Coinhive launched AuthedMine
after criticism from the media, the public, and after ad blockers and antivirus
vendors blocked its main domain because of the repeated abuse.
Conclusion:-
Cryptominer
tools don’t harm your computer, and nothing is stored on your hard drive, so
they can’t be considered to be malware in that sense. However, they can be
referred to as greyware, meaning they are identified as annoying software,
especially when they are set up to consume all of your CPU power.
From Many reports on
cryptojacking, many users said they are OK with websites mining Monero in the
background if they don't see ads anymore.
The
problem is that most of the places where cryptojacking has been spotted still
ran hoards of ads. Furthermore, a Trustwave report highlights
that running an in-browser miner is not actually free, and this may end up in
extra costs for a user's electricity bill.